Troubleshooting aethok.com HTTPS issue; atop
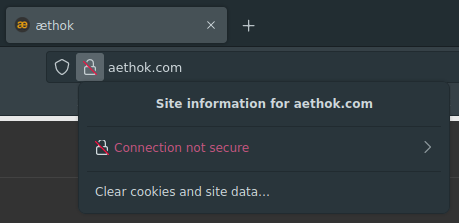
Today, I loaded the website for no good reason, and I get a “Connection not secure” message from Firefox. What gives? I thought I made sure that HTTPS works. Writing “https://” out explicitly before the domain name helps, but I really want it to be the only option. Let’s dig in to see what’s the problem.
Investigation
Let’s start by recalling what I did during the setup. The first thing it helps with is avoiding confusion during SSH-ing to the machine: my local IP keeps changing, so I need to make sure I have the current one white listed in the AWS security configuration. I’m so glad I’m writing these notes.
Aside: atop.
So, I SSH into aethok.com and immediately get sidetracked into looking for ways to see how the server has been since my last visit. That’s how I learn about the atop tool, and I save myself from attempting to develop anything of the sort. Neat!
Note to self: the website for atop has great intro documentation: screenshots with description. Cannot think of a better way to introduce a tool. Perhaps, the only improvement I could make is not to hide it under a tab called “Screenshots”.
The rest of this section reflects sections from that web page.
Memory
“The memory percentage (column MEM) shows the resident memory occupation by this process, because that is what matters when your system starts swapping.” – neat! For aethok.com it’s 0 for the past 90 days.
Misc
Exploring different processes really helps me understand how the system works.
For example, I ran atop on my dev machine too, and for that I needed to use
sudo, to get full information. So once it starts I do the following:
- press
zto pause the updates - press
/followed by “atop” to find the process - press
vto get misc information: including the PPID (parent PID) - press
Iand type the PPID to see who spawnedatop: surprisingly: I get nothing - press
/and pressEnterto clear the filter for “atop”: unsurprisingly,sudospawnedatop - press
Iand type the PPID ofsudo: I getbash - press
Iand type the PPID ofbash: I gettmux: server; this is because I usetmux.
The PPID for tmux: server is 1, which is systemd – the root process in
Linux that spawns all other processes.
I feel like I’ve learned something! Let’s move on now.
Command line
Looking at the output for my dev machine I learn that Firefox spawns a new process for each tab I have open on my machine. More knowledge! Neat!
Other notes
It seems that firefox is the only process directly spawned by cinnamon.
Another GUI program I have open is gnome-terminal, but the parent for that is
systemd. I also have three terminal windows, and the gnome-terminal process
has three bash children processes. So my guess is that during startup it
requests a daemon to be created by systemd and then when new terminals are
requested the daemon is asked to spawn a bash process for each. All windows
are probably owned by the daemon. Killing it closes all windows, which is why I
feel confident about that idea.
I wonder what’s the interface between gnome-terminal and bash… but that
would be an aside to the aside, so perhaps I should hold my horses a little bit.
For now.
Accumulated per program
This is really getting to the honey pot. In order to sort by cpu, mem, or disk,
I use s followed by p, or m followed by p, or d followed by p.
So to ask my server “how have you been?”, I can do atop and then zspmpdp.
Further distractions
Kernel process masquerading
Poking around made me discover process number two: [kthreadd]. Which lead me
to an article about kernel process masquerading. Some notes on the article:
cat /proc/<PID>/maps: “This location is normally where processes show
libraries they are linking to and where they mapped to in memory.”
cat /proc/<PID>/exe: “You can copy this file to a new location and have an
instant snapshot of the binary that started the process.”
Closing the atop aside
There’s also the netatop kernel module which enables network statistics too.
It would be cool to have a look at that too, but maybe some other time, given
that I haven’t even started looking at the main problem this article meant to
address.
Is the certificate outdated?
It doesn’t seem so. If this was the case, then the HTTPS version would not be working either. At this point, I’m thinking that I either never set up forcing of the use of HTTPS, or the setup has broken and needs some maintenance.
And reading until the end of my previous post it seems that I never set it up in the first place. So the solution should be just logging into CloudFlare and forcing HTTPS only access.
Enforcing HTTPS with CloudFlare
I naively thought that I could just find the option in the menus, once I log in to CloudFlare.
It turns out, I had to search for “cloudflare enforce https”, only to find a page that I’ve visited before. So I learn that my menu exploration skills were not up to the task, after all. The enforcement option is “hidden” in the “Edge Certificates” sub-menu of “SSL/TLS” menu.
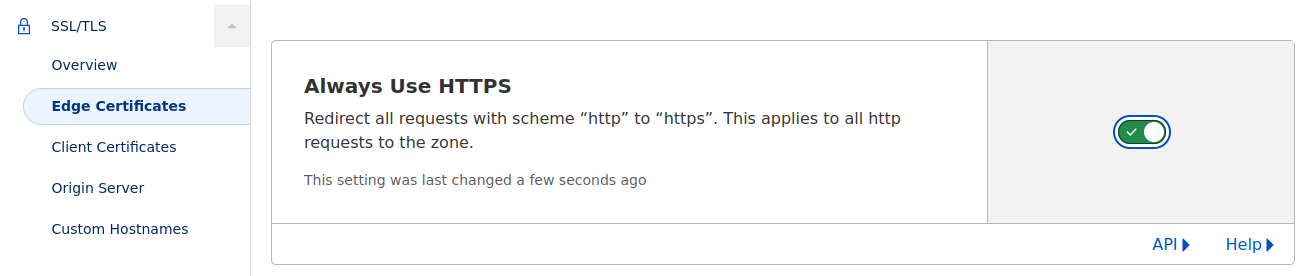
I toggle the switch, but reloading the page does not take me to the https version. Perhaps it takes some time for the change to take an effect. For now, I will keep my Firefox in “Don’t enable HTTPS-Only Mode” so that I can see if the problem reoccurs.
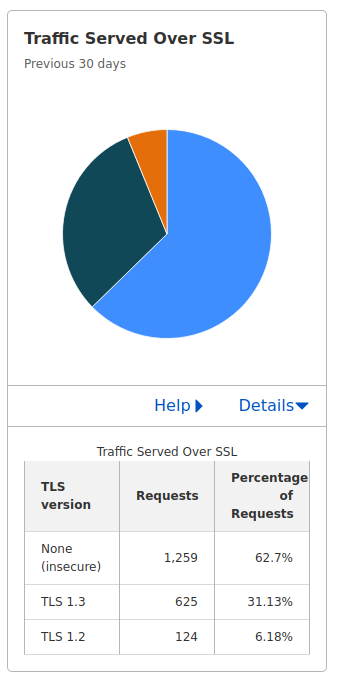
Additionally, looking at the statistics from CloudFlare, I can see that 60% of my traffic over the past month (until 20220714) has been insecure, 30% has been served over TLS 1.3, and 10% has been served over TLS 1.2. This is across 2000 requests. After some time passes, I expect the insecure part to drop to 0, if HTTPS is truly forced by CloudFlare.
Conclusion
My connection was not secure, just because I wasn’t enforcing it. I enabled a configuration setting in the CloudFlare account for aethok.com to enforce HTTPS, but that didn’t have an immediate effect (reloading the page in Firefox still shows it as insecure).
I’ll wait some time and revisit the issue, if it persists.